The New Era of AI in 2025: From Gemini 3 to Creative AIs
Learn about the best AI tools for 2025, including Nano...
We use cookies for our website to give you the most relevant experience by remembering your preferences. By clicking “accept”, you consent to use of ALL the cookies
This website uses cookies to improve your experience while you navigate through the website. Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. We also use third-party cookies that help us analyze and understand how you use this website. These cookies will be stored in your browser only with your consent. You also have the option to opt-out of these cookies. But opting out of some of these cookies may affect your browsing experience.
Necessary cookies are absolutely essential for the website to function properly. These cookies ensure basic functionalities and security features of the website, anonymously.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-functional | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category “Analytics”. |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category “Functional”. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category “Necessary”. |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category “Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category “Performance”. |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
Functional cookies help to perform certain functionalities like sharing the content of the website on social media platforms, collect feedbacks, and other third-party features.
Performance cookies are used to understand and analyze the key performance indexes of the website which helps in delivering a better user experience for the visitors.
Analytical cookies are used to understand how visitors interact with the website. These cookies help provide information on metrics the number of visitors, bounce rate, traffic source, etc.
Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads.
Other uncategorized cookies are those that are being analyzed and have not been classified into a category as yet.
Cyberia Tech, Inc. respects your privacy. This Privacy Policy explains how we collect, use, and share your information. By using our services, you agree to this policy. If any other agreements conflict with this Privacy Policy, the terms of those agreements prevail.
Cyberia Tech complies with the EU-US and Swiss-US Privacy Shield Frameworks for handling personal data from the EEA, UK, and Switzerland. In case of any conflict, the Privacy Shield Principles prevail. Learn more at Privacy Shield. Key Definitions
Information linked to an individual, transferred from the EEA, UK, or Switzerland to the U.S.
Data revealing race, religion, health, sexual orientation, and similar categories.
Effective Date: [ 2026 / 03 / 03 ]
Welcome to The Cyberia Tech ! By accessing or using our website or services, you agree to
comply with and be bound by these Terms of Use and our Privacy Policy. If you do not agree with
these terms, please do not use our Services.
Loading
0 %

Secure e-commerce is no joke. Just this month, the news broke about a significant data breach at luxury giant Louis Vuitton, affecting customers across the globe. This incident is a reminder that no online business, regardless of its size, is immune to cybercrime. For any entrepreneur or business leader, the idea of their online store being hacked is unsettling. You put effort into building your brand, nurturing customer relationships, and processing transactions. The thought of that trust being violated, and your hard work undone, is a genuine fear.
But the reality is, protecting your online store from cyber crime is important, it’s the core to your business’s growth and customer trust. This guide aims to move beyond just warnings and equip you with a practical understanding of the threats and, more importantly, the steps you can take to build a fortress around your digital storefront. Stay with us.
As history shows, the importance of secure e-commerce can’t be overlooked. Back in 2012, even the customer service-focused giant Zappos experienced a significant breach that compromised the personal data of millions. While credit card information remained safe, the lack of trust that followed was a powerful warning about the value customers place on the security of their information.

And the threat isn’t limited to multinational corporations. Consider the story shared by a frantic business owner on Reddit, a stark reminder of the personal impact of these attacks. After moving to a new, secure platform, they were repeatedly targeted:
“2 weeks in and we get hacked again. All products over the first 2 weeks of uploading deleted… Next day we spend the first 8 hours uploading our products back and fixing our store. Guess what happens next? Hacked again. With the 2 step verification process enabled the hacker was still able to get into the Shopify account and delete all our items and mess up the full layout of our shop.”
This personal account underscores the devastating reality that to protect your online store from hacking is not just a concept, but a very real and persistent concern that can directly impact your job and your customers’ trust.
By understanding these real-world scenarios, from large-scale data leaks to individual store compromises, we begin to truly grasp the multifaceted nature of the threats facing online businesses today. The key takeaway is clear: a proactive and comprehensive approach to secure e-commerce is no longer optional – it’s essential for survival in the digital marketplace.
Feeling a little anxious after reading those stories? That’s a normal reaction. Building a secure online store is an ongoing process, not a one-time fix. Here is a practical checklist to help you strengthen your defenses, starting today.
Think of these as the locks on your front door. Without them, you’re an easy target.
This is where many store owners get into trouble, often without realizing it. The tools that help you run your business can also be its biggest vulnerability.

Protecting your customers’ financial information is your most sacred duty as a merchant.
If the worst happens, your ability to recover depends entirely on your backup plan.
With a huge percentage of online shopping now happening on phones, your mobile e-commerce security can’t be an afterthought. Customers expect the same level of safety when they tap “buy now” on their phone as when they click it on a desktop. Ensure your website’s mobile version is not only responsive and easy to use but also fully secure. All the principles we’ve discussed, such as HTTPS, secure payment gateways, and data protection, apply just as much, if not more, to your mobile experience.

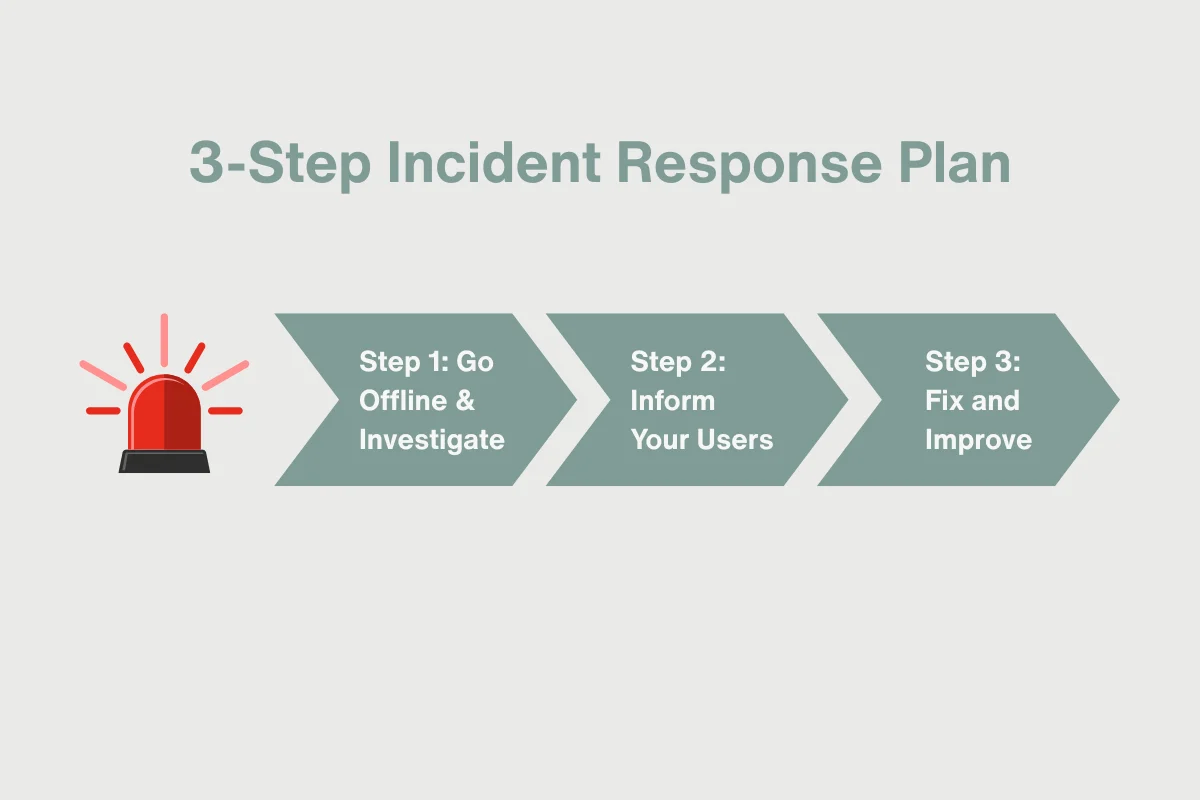
Maintaining a truly secure e-commerce environment means accepting that even with the best defenses, a breach can still happen. Your response in the immediate aftermath is critical for mitigating damage and retaining customer trust. Don’t panic; have a plan.
What is secure remote commerce?
Click to Pay, also known as Secure Remote Commerce (SRC), is a shared payment system that contributes to a more secure e-commerce experience by making online checkout faster. It saves you from having to enter your personal and card details on every new website, and it works on your computer, phone, or tablet.
What is encryption in e-commerce?
Think of encryption as locking your data in a digital safe. It converts your information into a secret code, and only those with the unique key to the safe can unlock and view it.
Ultimately, achieving secure e-commerce is a continuous process of vigilance, not a one-time task you can check off a list. The digital landscape and the threats within it are always evolving, which means our approach to security must evolve as well. By staying informed, being proactive with updates, and carefully managing every tool and app you connect to your store, you can build a resilient business that customers feel confident and safe shopping with. Your commitment to security is one of the most valuable investments you can make in your brand’s future.
This complex environment can be daunting. For expert guidance and personalized consultation on your cybersecurity posture, consider partnering with a trusted expert. At The Cyberia Tech, we’re here to be your dedicated IT partner, helping you implement the right strategies to protect your business.
You Can Get More Information!
