The New Era of AI in 2025: From Gemini 3 to Creative AIs
Learn about the best AI tools for 2025, including Nano...
We use cookies for our website to give you the most relevant experience by remembering your preferences. By clicking “accept”, you consent to use of ALL the cookies
This website uses cookies to improve your experience while you navigate through the website. Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. We also use third-party cookies that help us analyze and understand how you use this website. These cookies will be stored in your browser only with your consent. You also have the option to opt-out of these cookies. But opting out of some of these cookies may affect your browsing experience.
Necessary cookies are absolutely essential for the website to function properly. These cookies ensure basic functionalities and security features of the website, anonymously.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-functional | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category “Analytics”. |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category “Functional”. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category “Necessary”. |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category “Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category “Performance”. |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
Functional cookies help to perform certain functionalities like sharing the content of the website on social media platforms, collect feedbacks, and other third-party features.
Performance cookies are used to understand and analyze the key performance indexes of the website which helps in delivering a better user experience for the visitors.
Analytical cookies are used to understand how visitors interact with the website. These cookies help provide information on metrics the number of visitors, bounce rate, traffic source, etc.
Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads.
Other uncategorized cookies are those that are being analyzed and have not been classified into a category as yet.
Cyberia Tech, Inc. respects your privacy. This Privacy Policy explains how we collect, use, and share your information. By using our services, you agree to this policy. If any other agreements conflict with this Privacy Policy, the terms of those agreements prevail.
Cyberia Tech complies with the EU-US and Swiss-US Privacy Shield Frameworks for handling personal data from the EEA, UK, and Switzerland. In case of any conflict, the Privacy Shield Principles prevail. Learn more at Privacy Shield. Key Definitions
Information linked to an individual, transferred from the EEA, UK, or Switzerland to the U.S.
Data revealing race, religion, health, sexual orientation, and similar categories.
Effective Date: [ 2026 / 01 / 22 ]
Welcome to The Cyberia Tech ! By accessing or using our website or services, you agree to
comply with and be bound by these Terms of Use and our Privacy Policy. If you do not agree with
these terms, please do not use our Services.
Loading
0 %

Are you seeking information on general computer services that is useful? Exists a connection between embedded systems and General computing systems?
We’ll discuss each of these topics and how they’re related. In the desktop environment, we will also examine general purpose computers.
Technology and aesthetic considerations combine to encourage participation from end users. In any case, we’ll break down this topic for you to clear up any confusion.
This topic concerns computer hardware and software, which will let us accomplish various jobs. Please continue reading and commenting below with your thoughts on this.
Table of Contents
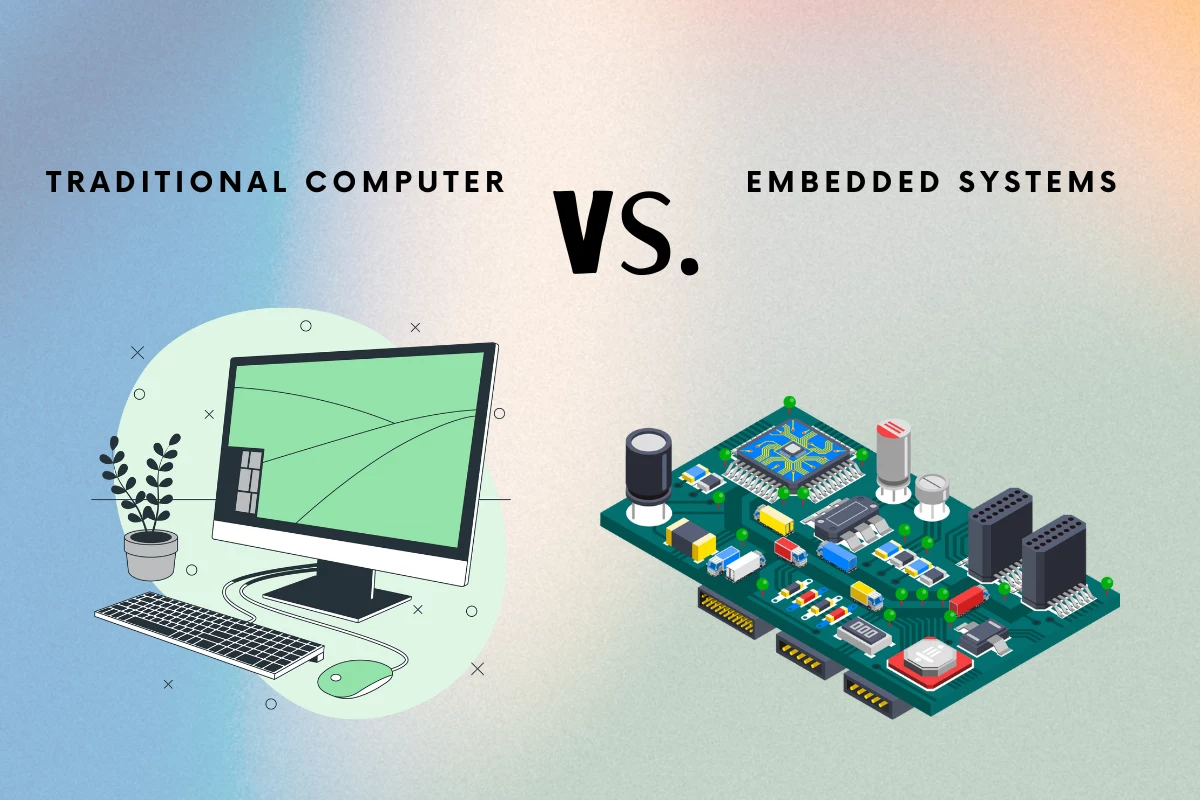
Both convey different kinds of information about computers and their parts, so that’s something to remember when discussing their differences.
Information about the device’s hardware and software functionality may be gleaned from the definition of standard computer services. Combining them yields a wide range of benefits for the user.
While hardware and software are involved in embedded systems, the critical difference is the added functionality they offer the end user.
All-purpose systems and embedded systems differ primarily in these ways. Particular distinctions exist between them, such as:
The computer provides the user with various functions through hardware and software.
The embedded system combines hardware and software but is for specific functionality operating without human incorporation.
As clear from the topic, we need human integration in general computing systems to perform tasks on a computer.
On the contrary, embedded systems perform tasks without human bits’ help and run services based on operating codes.
In computer services, hardware and software are the two main categories of components.
Hardware, software, and firmware are the three components that make up the embedded system.
As we discussed before, computers may be used in various contexts and accomplish multiple activities. Put another way, embedded only does a particular set of things.
Suppose you’re thinking about getting a computer. In that case, you should know that there’s more to computing systems than just the embedded system, including how money is exchanged, because there are so many more options available to you in a digital environment.
The accessories usable in a computer are the mouse, keyboards, printer, hard disks, etc.
On the other hand, the embedded peripherals are a communication interface and multi cards (SD cards, flash, etc.).
Everything in a computer can be reprogrammed to a different goal, while embedded systems are designed to serve one purpose exclusively.
More than only the embedded devices, many computer-based services require significant amounts of operating power. We all know that in the world of embedded systems, only a handful of critical operations must be in working order, but things are constantly changing in the world of computers.
These are the most noticeable variations, but there are further distinctions that we shall detail below.
Applications. The provided options bring better performance. Widgets also come in handy to save time and reduce using OEMs. Depending on a library of pre-made widgets, this complete Kit helps limited programming development to experience a rapid market launch.
We can elaborate on the differences in functionality between the two and help you make an informed decision.
Comparing standard computer services to the one-of-a-kind services as bespoke software offered by embedded devices is like comparing apples and oranges, as the former will naturally be more complex.
Embedded has always been a part of the system itself; it has no external interface and must complete its task within a predetermined time. In terms of physical dimensions, they are pretty diminutive.
However, computers need more user interfaces and more installation options. Tasks that must be implemented may not need a precise time or may take several days to execute and complete.
In general, it’s comforting to know that computers are a later innovation than embedded systems and, as a result, have more room for data storage.

Were you aware of the many forms of computers that you encounter regularly? A computer, at its most elemental, is just a mechanism that takes in jumbled bits of information and reassembles them in a way that makes sense to the software.
The computer also categorizes elements and structures of the processing data to understand their usability and speed to divide them into different types:
With regards to computers, this is the first and foremost. A PC is short for “personal computer,” which describes what it is. This kind of computer has lightning-fast processing and networking speeds. There is a wide range of sizes and shapes available. The desktop form factor is the most common for this system, but it is also known as a laptop, processor, network, etc.
The primary purpose of these general-purpose computers is to display media content such as text and images, speech, animation, and video clips.
It has a network of servers and can administer our systems with a minimal outlay of cash. Minicomputer, with a strong network for controlling major websites online, was its original billing.
A system of this type is a massive, quick, robust, and powerful computer that can process hundreds of structures per second and is, therefore, exceptional. It’s the ideal computer system, down to the last detail, and has much storage space. The aviation and oil industries regularly employ this kind of computer.
We’re talking about the supercomputers and networks used by industries and institutions that rely on lightning-fast processing and communications. Many institutions, including governments and significant colleges, have adopted this system.
Connectivity across various IT services is crucial to an integrated computer. Being an engineer entails making connections between seemingly unrelated fields. They see it as necessary to use it so that their operating system can perform better.
In integration systems, it belongs to a different class:
It’s about connecting one system to another to transfer various functionality, but it does not move more than one functionality.
It isn’t easy to manage the different systems in the long term, but this method is usable and efficient for simple integration.
It is used for a standard interface and allows the sub-system to have one interface to connect.
Another aspect of data integration in a computer system is transforming data from its native format into a standard one.
Thus far, we’ve discussed integrated computer system examples and given you a clear perspective of many scenarios. This system has a significant function on the desktop and is helpful in computing and engineering. Investing in such a system requires mathematical modeling due to the importance of the organizational field in the overall integration.
The information must be kept between subsystems and critical elements in the teacher’s section.
In this topic, we tried to give you potential information about general computing systems and why learning and having an idea about general purpose computers are helping us.
We tried to discuss various aspects. We checked and reviewed the definition of an embedded system and compared it with general computer services.
We find out that these two have some issues in common, but the major part was discussing their differences.
Most of this article includes a review of these two issues because of their diagnosis and efficiency in a computer environment. Please give us your idea and leave us a message. 🙏

What is a computer services?
Computer services refer to the various aspects related to the use of a computer. This includes the information stored in the computer, the personnel who support the computer system, as well as the functions of computer time, data processing, and storage.
What are some computer services?
7 IT Service Examples
Cloud services, backup and disaster recovery, network security, help desk support, managed print services, computer training, and IT consulting are all available.
What is general computer?
A general-purpose computer is one that is designed to do a wide range of functions. General-purpose computers include desktop computers and laptop computers. They may be used to, among other things, access the internet. Visit the World Wide Web (WWW).
What are the general types of computer?
Computers are classified according to their size.
Supercomputers.
Computers that run on mainframes.
Minicomputers.
Microcomputers or personal computers (PCs).
You Can Get More Information!
